Website Security Vulnerabilities: Identify & Resolve
The website of your company is the identity of your business on the cyberspace. To ensure that your business is accessible throughout the year, you need to have an effective website. However, just like the bricks and mortar business is prone to physical and natural threats; the website also faces a number of security issues. There are more than hundreds of issues and threats which have the ability to affect the stored data and overall structural website. This article talks about the most popular security threats that your business might be ignoring:
What Are Web Application Vulnerabilities?
Web application vulnerabilities are security issues found in websites or web application code that allow criminals to break into systems. Web application weaknesses allow criminals to break in and access private information or damage business systems.
Some common examples include:
- Cross-site scripting (XSS)
- SQL injection
- Broken authentication
Impact of Security Breaches
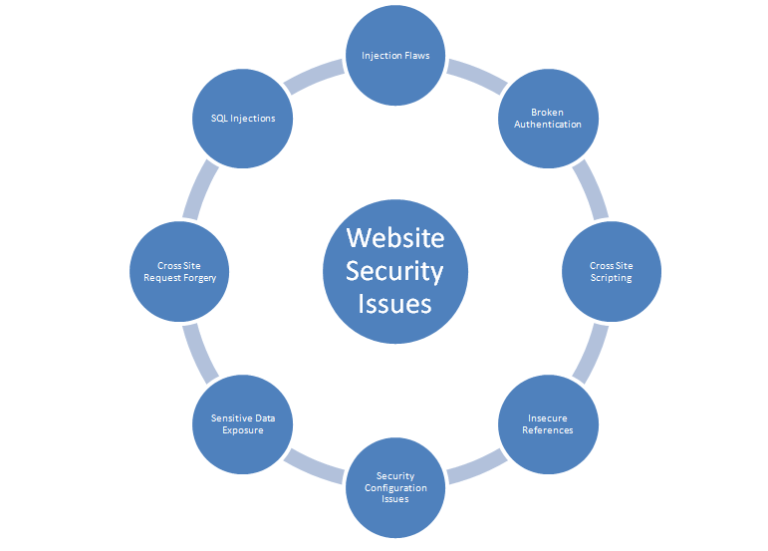
1) Injection Flaws
This issue could arise due to the failure filtering of non-trusted input. Whilst designing or updating the website, when unfiltered data is passed to the SQL server, browser, to the LDAP server or to anywhere else, this issue is bound to arise. The hackers and attackers could inject various commands to the given entities, and eventually, it results in loss of data. It means that all the inputs in a dynamic website need to be filtered which could be a very difficult and long process. This implies that if the website has a thousand entries per day, cross-checking 999 will still leave the scope of vulnerability within the system.
Possible Solution
The basic rule will be to ensure validation of all the inputs and not to completely trust from any user.
2) Broken Authentication
This aspect consists of a number of issues all rolled into a single issue that could be described as broken authentication. Some of the most common authentication related issues could include:
- The URL of the website could have session ID which could be leaked
- The unencrypted passwords issues in transit or storage
- For some hackers, gaining access is easier due to trivial session ID’s
- Fixing the sessions could be possible
- Without SSL or proper security, hijacking the sessions could be really easy for the hackers
Possible Solution
The users could be validated for ensuring that spoofing into the protected areas or circumvention the security features is restricted.
3) Cross-Site Scripting:
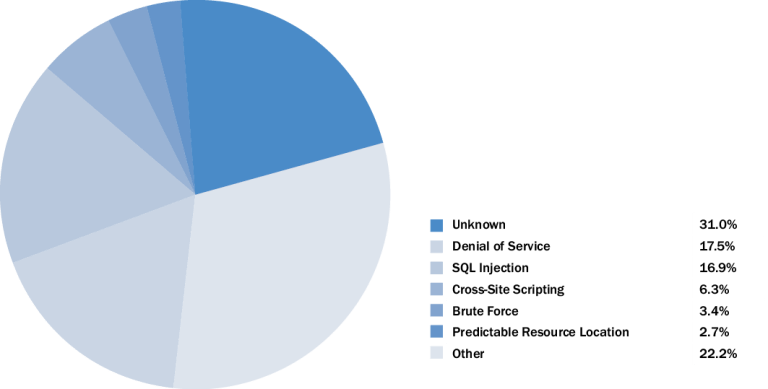
XSS as it is generally called targets the users by injecting a code which is most generally a client-side script like JavaScript within the web application’s output. The overall concept is simple: to manipulate the scripts at the client’s side to ensure that execution is carried out in the manner desired by the attacker. If your website is attacked, the attacker could use XSS to execute the scripts in the browser which would eventually result in hijacking the sessions, destabilizing the website, defacing the interface, or even redirect the users to other malicious or spam-based websites. The aftermath of the attack has been provided in the given pie chart.
Possible Solution
Any malicious attempt to exploit the vulnerability of the system should be prevented. For example, the websites created by Process Venue are screened and methods are fitted into place for prevention of such acts.
4) Insecure References:
Insecure direct object reference is a condition where a web application exposes or transfers the reference to any internal implementation object. If your website is attacked, the attacker could take use of the reference, and accordingly, if the authorization is not enforced or broken, the attacker would have direct access to the objects which should be rather closed out or secluded from any external parties. Let’s take an example: if the code has a download.php module that reads and provides authorization to the user to download a multiple or single files by taking use of a CGI parameter for specifying the file name (something like download.php?file=something.txt). Due to any reason, the developer could omit the authorization from the code. This means that the attacker now knows that any file from the system could be downloaded with the PHP access.
Possible Solution
The direct references should be exposed to database structures for ensuring that SQL statements and other database processes only allow authorized records to be shown.
5) Security Configuration Issues:
This is particularly based on the maintenance related issues which your website might be facing. When you do not pay enough heed towards website application configuration, the security misconfiguration issues might arise. For various applications, frameworks, application servers, web servers, database servers, and platforms, the secure configuration has to be defined and deployed. Any short measures in this area would result in complete compromise of the system and database of the network.
Possible Solution
By having the maintenance related jobs performed by in-house experts or by outsourcing it to an efficient third-party vendor.
6) Sensitive Data Exposure:
The overall concept of The overall concept of website security is based on crypto and resource protection. Your website should be secured in such a manner that sensitive data should be protected at all the times, even when it is in transit or put on rest. There cannot be any half-measures or exceptions to that. Any information related to credit cards, user passwords could be attacked in transit by the attackers, and eventually, it could result in loss of data due to weak hashing algorithm used by the developers.
Possible Solution
The coding process should be impeccable since the attackers don’t break crypto directly; the database is broken in specifically during transit or at rest.
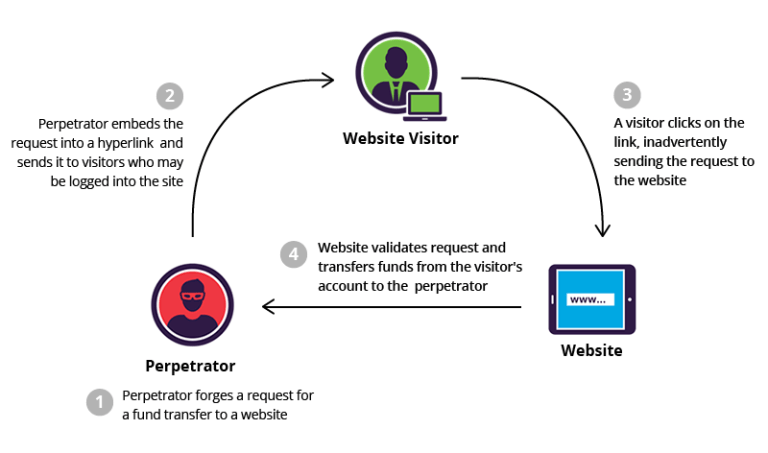
7) Cross-Site Request Forgery:
It is a malicious exploit of a website where unauthorized commands originate from a user which is trusted by the web application. It is different from XSS where the user’s trust for a particular website was exploited; here, the trust of a site on the browser is exploited by the attackers. There are various examples when websites of large companies like Netflix and ING Direct have been affected by the attackers through CSRF.
Possible Solution
Having proper security checks and security audits in place will help in reducing such incidents.
8) SQL Injections:
It is another common way of attacking the website where the attacker attempts to use the application code to access the content on your website. If this attack is successful, the attacker has direct access to the information stored in the back-end database which could be ultimately used to amend the database. It is one of the most common ways of attacking the websites.
Possible Solution
Encrypting the data and cleaning or validating the inputs could be the best ways of preventing such attack.
As a business organization, you are ought to have certain security-related troubles for your website. Process Venue cares for your business needs and ensures that your website security-related issues are taken care of. Our team of experienced professionals works across the year for assuring complete protection of your website from the external attackers.
Are there any other probable security issues which you might have faced, and have been able to rectify them? Tell us about that in the comments.
Why Choose ProcessVenue for Web Security Vulnerabilities
ProcessVenue uses advanced tools to locate and repair website security weaknesses, keeping businesses safe from cyber attacks. Our professionals thoroughly examine your website security to defend your digital data and design unique security solutions for your online system.
With ProcessVenue, you benefit from:
- We excel at finding web application security issues and fixing them.
- Our service helps safeguard your critical business information
- We stop website security problems before they start through active protection measures.
- Our website security tools work naturally with your daily business processes.
Conclusion
Managing website security problems helps your business stay safe and keeps your customers confident in your operations. Identifying and solving security problems early helps protect your information and business systems while ensuring smooth and protected daily operations. Your current investment in full website security systems reduces possible threats and makes your entire protection system more effective.
Frequently Asked Questions
What is an internet security threat?
An internet security threat is a possible attack designed to breach digital data or systems without user authorization. Multiple types of cyberattacks, are included in the threat, including malware, phishing, and ransomware.
Why is website security important for businesses?
Online security prevents data theft, builds customer trust, and helps businesses remain reliable online. Websites need strong security protection to prevent attacks and maintain the security of their data and money.
How do I identify vulnerabilities in my website?
We use website security scans with specialized tools to identify security issues on our website. These scans look for outdated software programs, weak spots in web applications, and unguarded entry points that hackers might use to break in.
Are small businesses at risk of website security vulnerabilities?
Yes, small businesses are often targeted due to the misconception that they have weaker security measures. Small businesses face the same risks of website security vulnerabilities as larger companies and should prioritize strong website protection.
What are the benefits of outsourcing website security management?
Outsourcing website security management ensures expert protection against web security vulnerabilities. It allows businesses to leverage specialized knowledge for proactive monitoring, timely updates, and effective responses to cyber threats, thus reducing potential risks.
What certifications or standards should a secure website comply with?
A secure website should comply with data protection services standards such as SSL/TLS certificates for encrypted connections, PCI-DSS compliance for payment security, and GDPR for data protection, ensuring robust database security and user privacy.
How does ProcessVenue address website security vulnerabilities?
ProcessVenue provides comprehensive web security solutions, addressing website security vulnerabilities through regular assessments, timely updates, and specialized website vulnerability management. Their team ensures that all aspects of a website, including data protection and application security, are fortified to prevent unauthorized access and data breaches.